12 Termux Tools for Ethical Hacking
12 Termux Tools for Ethical Hacking - Tool-X, Metasploit, Nmap, Wireshark, SQLMap, Social Engineering Toolkit, Nikto, Hydra, Zphisher and more.
This article provides a comprehensive guide to the top 12 Termux tools for ethical hacking on your Android device.
Termux is an application that turns your smartphone into a mini-computer, allowing you to run various cybersecurity tools.
The guide covers both classic tools, such as Metasploit and Nmap, as well as newer tools like Zphisher.
Each tool is explained in a straightforward manner, with step-by-step instructions on how to set up and use them effectively.
By reading this guide, you'll be able to transform your Android device into a powerful tool for ethical hacking.
This is a great way for beginners to get started in the world of cybersecurity, as the guide helps you learn about ethical hacking in a safe and responsible manner.
Ethical hacking is a crucial skill in today's digital landscape, as it allows you to identify and fix security vulnerabilities before they can be exploited by malicious actors.
This guide provides a valuable resource for anyone interested in enhancing their ethical hacking abilities on their Android device.
Simplified Setup: The tool simplifies the installation process, allowing you to set up various hacking tools without the need to install each one individually.
Regular Updates: Tool-X is regularly updated with the latest hacking tools, ensuring that you always have access to the most cutting-edge resources for your ethical hacking activities.
Organized Interface: The tool presents a user-friendly menu with different sections, such as Information Gathering, Checking for Weaknesses, and Cracking Passwords, making it easy to navigate and access the desired tools.
Versatility: Tool-X includes tools for testing the security of WiFi networks, providing a comprehensive solution for your ethical hacking needs.
User-Friendly Interface: With the simple command "msfconsole," you can access Metasploit's powerful features and feel like a true cybersecurity expert.
Comprehensive Testing Capabilities: Metasploit enables you to scan networks, test phishing emails, and perform other essential cybersecurity tasks.
Professional-Grade Tool: Metasploit is widely used by security professionals to identify and address security weaknesses, ensuring the safety of their systems.
Android Compatibility: You can now leverage the power of Metasploit on your Android device by using the Termux app, making it accessible and convenient.
Efficient Network Mapping: Nmap allows you to map out an entire network, identifying potential weak points that need to be addressed.
Ease of Use: Despite its powerful capabilities, Nmap is relatively simple to use, with basic commands readily available in the Termux app on your Android device.
Advanced Security Testing: Nmap provides ethical hackers with the tools they need to plan and execute their next security testing steps effectively.
Indispensable for Ethical Hacking: Any good ethical hacker will want to have Nmap in their toolkit, as it is an essential tool for keeping computer networks and devices safe.
Advanced Filtering: The tool allows you to apply filters to focus on specific types of network traffic, such as DNS requests, streaming data, and website logins.
Robust Network Analysis: Wireshark brings robust network analysis capabilities to your Android device, making it an invaluable tool for investigating network issues and understanding communication protocols.
Hacker Attack Detection: With Wireshark, you can detect and investigate potential hacker attacks by closely monitoring network activities.
Portable Network Visibility: Having Wireshark in your mobile toolkit gives you the power to gain deep visibility into network activities, no matter where you are.
Sensitive Data Retrieval: If vulnerabilities are found, SQLMap can be used to extract sensitive data, such as passwords, from the targeted database.
Comprehensive Weakness Detection: The tool helps you uncover a wide range of SQL injection vulnerabilities, allowing you to strengthen the security of your databases.
Streamlined Exploitation: SQLMap simplifies the process of exploiting SQL injection flaws, making it easier for ethical hackers to demonstrate the impact of these vulnerabilities.
Database Security Strengthening: By using SQLMap to find and fix SQL injection weaknesses, you can proactively secure your databases against potential attacks.
Technique Exploration: Ethical hackers use SET to learn about the various social engineering techniques that malicious actors may employ, allowing them to develop effective countermeasures.
Human Factor Education: By understanding social engineering, ethical hackers can train people to recognize and avoid falling for clever exploits, addressing the human element in security.
On-the-Go Learning: Running SET on the Termux app gives ethical hackers the ability to learn about social engineering techniques and how to mitigate them, wherever they may be.
Comprehensive Security Enhancement: Ultimately, SET helps address the human factor in security, empowering ethical hackers to better protect organizations and individuals against social engineering attacks.
Detailed Reporting: After scanning a website, Nikto provides a detailed report of the identified issues, allowing you to prioritize and address them effectively.
Auditing Capabilities: You can use Nikto to assess the security posture of your own websites, as well as help secure others' sites with their permission.
Mobility and Convenience: By running Nikto on the Termux app, you can conduct comprehensive website security scans from your Android device, wherever you may be.
Proactive Security Enhancement: Utilizing Nikto can help you stay ahead of potential attackers by addressing vulnerabilities before they can be exploited.
Beginner-Friendly Tutorials: The toolkit comes with step-by-step tutorials to guide you through the basics of ethical hacking, making it an excellent resource for those new to the field.
Engaging Inspiration: Inspired by the popular Mr. Robot TV show, the Fsociety Toolkit offers an immersive and engaging way to learn about hacking and cybersecurity.
Android Compatibility: You can access the Fsociety Toolkit on your Android device, allowing you to explore hacking concepts and techniques on-the-go.
Ethical Hacking Exploration: By using the Fsociety Toolkit, you can safely and legally explore the world of ethical hacking, gaining valuable skills and insights.
Versatile Access Attempts: The tool can be used to target various services and protocols, including FTP, SSH, HTTP, and more, expanding its utility for ethical hacking.
Responsible Usage: When used responsibly by ethical hackers, Hydra can be an invaluable tool for identifying and addressing security vulnerabilities.
Termux Compatibility: The Termux version of Hydra allows you to run the password-cracking tool conveniently on your Android device, providing mobile penetration testing capabilities.
Fsociety Toolkit Integration: Hydra is seamlessly integrated into the Fsociety Hacking Toolkit, making it easily accessible and part of a comprehensive suite of ethical hacking tools.
Consent-Based Usage: Zphisher is meant to be used only with the consent of the target audience, not for real credential theft or hacking activities.
Experiential Learning: By using Zphisher, you can gain firsthand experience in understanding how phishing attacks work and the importance of verifying the authenticity of login pages.
Awareness Raising: Properly used, Zphisher can be a valuable tool for educating people about the dangers of phishing and the need to be vigilant when providing their login credentials online.
Android Compatibility: You can access and use Zphisher on your Android device, making it a convenient tool for security awareness and testing purposes.
Demonstrate Anonymity Challenges: The tool highlights how difficult it can be to maintain complete anonymity online based solely on an IP address or website.
Comprehensive Geolocation Data: IPTracer leverages various IP geolocation databases to provide detailed location information, including latitude, longitude, and even the specific street address.
User-Friendly Interface: The tool offers a straightforward and intuitive interface, making it easy for users of all skill levels to explore the capabilities of IP geolocation.
Android Accessibility: With IPTracer available on your Android device, you can conveniently uncover the physical location of online entities wherever you go.
Proximity Range Estimation: The tool can also estimate the proximity range of the device you're tracking, providing even more valuable location details.
Useful for Security Research: When used responsibly and ethically, Seeker can be an incredibly valuable tool for security research and understanding the implications of device tracking.
Intuitive Interface: The tool offers a straightforward and user-friendly interface, making it accessible for users of all skill levels.
Android Compatibility: You can access and utilize Seeker on your Android device, allowing you to explore its capabilities on-the-go.
Top 10 Termux Tools Every Ethical Hacker Should Know
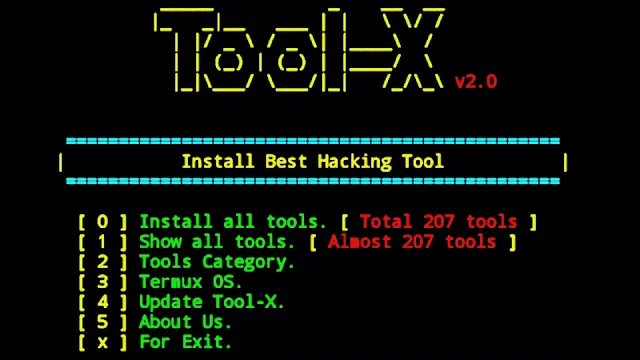
1. Tool-X
Tool-X is a one-stop solution for ethical hackers looking to enhance their cybersecurity skills on their Android devices.
This powerful tool collects over 100 hacking tools in a single place, making it easy to access and utilize a wide range of resources for your ethical hacking endeavors.
With its extensive tool collection, simplified setup, and user-friendly interface, Tool-X is a valuable resource for anyone interested in ethical hacking on their Android device.
Whether you're a beginner or an experienced ethical hacker, this tool can help you enhance your cybersecurity skills and stay ahead of the curve.
Key Features:
Extensive Tool Collection: Tool-X provides access to a diverse range of hacking tools, including popular options for information gathering, vulnerability testing, and password cracking.
Simplified Setup: The tool simplifies the installation process, allowing you to set up various hacking tools without the need to install each one individually.
Regular Updates: Tool-X is regularly updated with the latest hacking tools, ensuring that you always have access to the most cutting-edge resources for your ethical hacking activities.
Organized Interface: The tool presents a user-friendly menu with different sections, such as Information Gathering, Checking for Weaknesses, and Cracking Passwords, making it easy to navigate and access the desired tools.
Versatility: Tool-X includes tools for testing the security of WiFi networks, providing a comprehensive solution for your ethical hacking needs.
How to install Tool-x in Termux:
pkg update && pkg upgrade -ypkg install gitgit clone https://github.com/Rajkumrdusad/Tool-X.gitcd Tool-Xchmod +x install.aexsh install.aex./install.aexHence the Tool-X is installed in your Termux. To run this tool, type the below command.
Tool-XRelated article - How to install Tool-X in Termux
2. Metasploit Framework
Metasploit is an open-source tool that is widely used by ethical hackers to test the security of networks and systems.
This powerful tool can be a valuable asset for anyone interested in enhancing their cybersecurity skills, especially when used in conjunction with the Termux app on your Android device.
By using Metasploit on your Android device, you can gain a deep understanding of ethical hacking and take proactive steps to secure your systems and networks.
Whether you're a beginner or an experienced cybersecurity enthusiast, Metasploit is a tool that can help you stay ahead of the curve and protect your digital assets.
Key Features:
Extensive Exploit and Payload Database: Metasploit boasts over 3,500 exploits and payloads, allowing you to test a wide range of security vulnerabilities.
User-Friendly Interface: With the simple command "msfconsole," you can access Metasploit's powerful features and feel like a true cybersecurity expert.
Comprehensive Testing Capabilities: Metasploit enables you to scan networks, test phishing emails, and perform other essential cybersecurity tasks.
Professional-Grade Tool: Metasploit is widely used by security professionals to identify and address security weaknesses, ensuring the safety of their systems.
Android Compatibility: You can now leverage the power of Metasploit on your Android device by using the Termux app, making it accessible and convenient.
How to install Metasploit Framework in Termux:
pkg update && pkg upgrade -ypkg install unstable-repopkg install metasploitmsfconsoleRelated Article - How to Install Metasploit in Termux
3. Nmap
Nmap, short for Network Mapper, is a powerful tool that every ethical hacker should have in their arsenal.
This versatile tool is perfect for thoroughly investigating computer networks and devices to ensure their security.
By using Nmap on your Android device, you can take a proactive approach to network security and identify vulnerabilities before they can be exploited.
Whether you're a beginner or an experienced ethical hacker, Nmap is a must-have tool that can help you stay ahead of the curve in the ever-evolving world of cybersecurity.
Key Features:
Comprehensive Network Scanning: Nmap can quickly scan for open ports, detect the operating system being used, and perform a wide range of advanced security tests.
Efficient Network Mapping: Nmap allows you to map out an entire network, identifying potential weak points that need to be addressed.
Ease of Use: Despite its powerful capabilities, Nmap is relatively simple to use, with basic commands readily available in the Termux app on your Android device.
Advanced Security Testing: Nmap provides ethical hackers with the tools they need to plan and execute their next security testing steps effectively.
Indispensable for Ethical Hacking: Any good ethical hacker will want to have Nmap in their toolkit, as it is an essential tool for keeping computer networks and devices safe.
How to install Nmap in Termux:
pkg update && pkg upgrade -ypkg install curlpkg install nmapOnce installed, typing "nmap" will open the utility right in Termux.
4. Wireshark
Wireshark is a powerful network analysis tool that allows you to inspect and examine the data flowing across networks in great detail.
By running Wireshark on your Android device using the Termux app, you can gain valuable insights into the network traffic happening around you.
By using Wireshark on your Android device, you can unlock a wealth of information about the networks you interact with, empowering you to make more informed decisions and take proactive measures to ensure the security of your digital environment.
Key Features:
Detailed Network Monitoring: Wireshark enables you to capture and analyze network packets, providing a comprehensive view of the data moving across your network.
Advanced Filtering: The tool allows you to apply filters to focus on specific types of network traffic, such as DNS requests, streaming data, and website logins.
Robust Network Analysis: Wireshark brings robust network analysis capabilities to your Android device, making it an invaluable tool for investigating network issues and understanding communication protocols.
Hacker Attack Detection: With Wireshark, you can detect and investigate potential hacker attacks by closely monitoring network activities.
Portable Network Visibility: Having Wireshark in your mobile toolkit gives you the power to gain deep visibility into network activities, no matter where you are.
5. SQLMap
SQLMap is a powerful tool that ethical hackers rely on to automatically detect and exploit SQL injection vulnerabilities in websites and applications they have permission to test.
This invaluable tool can help you identify and address security weaknesses before they can be exploited by malicious actors.
With SQLMap in your toolkit, you can take a proactive approach to database security and ensure that your systems are protected against SQL injection attacks.
Whether you're a seasoned ethical hacker or new to the field, this tool can be a valuable asset in your efforts to maintain the integrity and confidentiality of your organization's data.
Key Features:
Automated SQL Injection Testing: SQLMap employs a variety of techniques to systematically test for and identify SQL injection flaws in your systems.
Sensitive Data Retrieval: If vulnerabilities are found, SQLMap can be used to extract sensitive data, such as passwords, from the targeted database.
Comprehensive Weakness Detection: The tool helps you uncover a wide range of SQL injection vulnerabilities, allowing you to strengthen the security of your databases.
Streamlined Exploitation: SQLMap simplifies the process of exploiting SQL injection flaws, making it easier for ethical hackers to demonstrate the impact of these vulnerabilities.
Database Security Strengthening: By using SQLMap to find and fix SQL injection weaknesses, you can proactively secure your databases against potential attacks.
How to install SQLMap In Termux:
pkg update && pkg upgrade -yapt install python python2pkg install gitgit clone https://github.com/sqlmapproject/sqlmapcd sqlmapchmod +x sqlmap.pypython2 sqlmap.pyOnce setup, you can launch sqlmap.py and leverage this powerful web ethical hacking tool for finding and exploiting those subtle SQLi vulnerabilities!
Related Article - How to install and use SQLMap in Termux
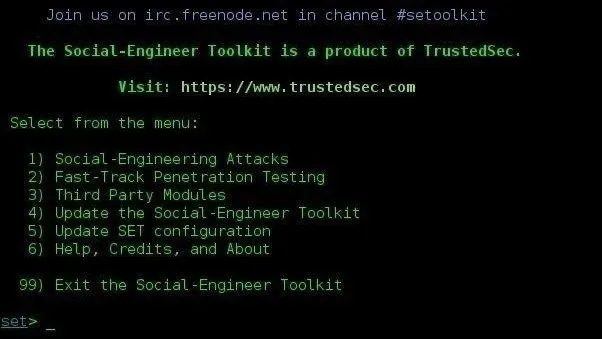
6. Social Engineering Toolkit (SET)
The Social Engineering Toolkit (SET) is a powerful tool that enables ethical hackers to learn about and understand the techniques used in social engineering attacks.
Social engineering tricks people into revealing sensitive information, which can be a significant security vulnerability.
By using the Social Engineering Toolkit on your Android device, you can gain valuable insights into the world of social engineering and take proactive steps to enhance the overall security of your systems and networks.
Key Features:
Simulated Attacks: SET can create realistic fake websites and malicious emails to test whether people fall for social engineering tactics, but only with prior consent.
Technique Exploration: Ethical hackers use SET to learn about the various social engineering techniques that malicious actors may employ, allowing them to develop effective countermeasures.
Human Factor Education: By understanding social engineering, ethical hackers can train people to recognize and avoid falling for clever exploits, addressing the human element in security.
On-the-Go Learning: Running SET on the Termux app gives ethical hackers the ability to learn about social engineering techniques and how to mitigate them, wherever they may be.
Comprehensive Security Enhancement: Ultimately, SET helps address the human factor in security, empowering ethical hackers to better protect organizations and individuals against social engineering attacks.
How to install Social Engineering Toolkit in Termux:
pkg update && pkg upgrade -yapt install curl -y curl -LO https://raw.githubusercontent.com/Hax4us/setoolkit/master/setoolkit.shsh setoolkit.shAfter finishing the above process, type the following command.
cd setoolkit./setup.py install./setoolkitOnce setup, you can launch setoolkit and start building out crafty social engineering campaigns. This is fantastic for evaluating vulnerabilities in the human element and bolstering defenses!
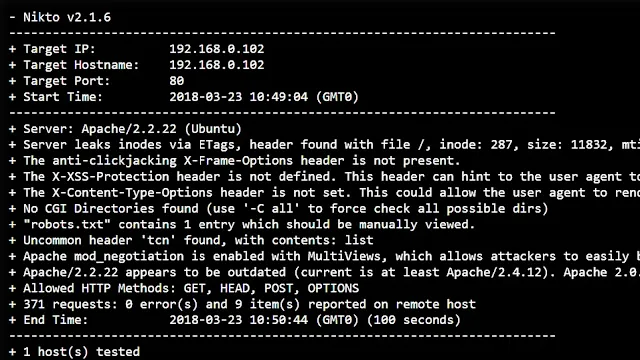
7. Nikto
Nikto is a powerful tool that can help you identify and address over 6,500 potential security vulnerabilities in websites.
This comprehensive scanner can be an invaluable asset for anyone looking to ensure the security of their online presence.
With Nikto in your toolkit, you can take a proactive approach to website security and ensure that your online presence is protected against a vast array of known vulnerabilities.
Whether you're a website owner, a security professional, or simply someone who values the importance of online security, Nikto can be a valuable tool in your efforts to maintain a secure and robust digital environment.
Key Features:
Extensive Vulnerability Detection: Nikto scans websites for a wide range of security issues, including outdated software, missing security configurations, and file upload vulnerabilities.
Detailed Reporting: After scanning a website, Nikto provides a detailed report of the identified issues, allowing you to prioritize and address them effectively.
Auditing Capabilities: You can use Nikto to assess the security posture of your own websites, as well as help secure others' sites with their permission.
Mobility and Convenience: By running Nikto on the Termux app, you can conduct comprehensive website security scans from your Android device, wherever you may be.
Proactive Security Enhancement: Utilizing Nikto can help you stay ahead of potential attackers by addressing vulnerabilities before they can be exploited.
How to install Nikto in Termux:
apt update && apt upgradepkg install gitpkg install perlgit clone https://github.com/sullo/nikto.gitcd niktocd programperl nikto.pl -h <Target Website>Once installed, just swap out <Target Website> for your desired domain. This will initiate a comprehensive Nikto vulnerability scan!
Use these findings to harden web servers and applications well in advance. Your future self will thank you!
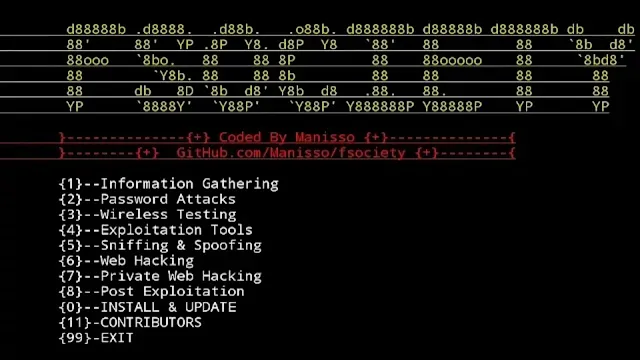
8. Fsociety
The Fsociety Hacking Toolkit is an exciting collection of over 30 hacking tools and resources designed to help you learn about computer security and ethical hacking.
Whether you're a beginner or an experienced security enthusiast, this toolkit can be a valuable asset in your exploration of the cybersecurity landscape.
Whether you're interested in enhancing your cybersecurity knowledge, pursuing a career in ethical hacking, or simply satisfying your curiosity, the Fsociety Hacking Toolkit can be a fantastic resource to have on your Android device.
Key Features:
Comprehensive Tool Collection: The Fsociety Toolkit includes a wide range of utilities for network scanning, password cracking, and various other hacking techniques, all in one convenient package.
Beginner-Friendly Tutorials: The toolkit comes with step-by-step tutorials to guide you through the basics of ethical hacking, making it an excellent resource for those new to the field.
Engaging Inspiration: Inspired by the popular Mr. Robot TV show, the Fsociety Toolkit offers an immersive and engaging way to learn about hacking and cybersecurity.
Android Compatibility: You can access the Fsociety Toolkit on your Android device, allowing you to explore hacking concepts and techniques on-the-go.
Ethical Hacking Exploration: By using the Fsociety Toolkit, you can safely and legally explore the world of ethical hacking, gaining valuable skills and insights.
How to install Fsociety in Termux:
pkg update && pkg upgradepkg install gitpkg install python2git clone https://github.com/Manisso/fsociety.gitcd fsocietychmod +x install.shOnce setup, access the toolkit by typing:
python2 fsociety.pyNow you can launch various utilities directly from the retro command line! It's fantastic for bringing that Mr. Robot flair while expanding your ethical hacking arsenal.
9. Hydra
Hydra is a formidable password-cracking tool that is part of the Fsociety Hacking Toolkit.
This powerful program can rapidly attempt numerous username and password combinations to gain unauthorized access, such as brute-forcing into FTP servers using lists of credentials.
By leveraging Hydra within the Fsociety Hacking Toolkit on your Android device, you can enhance your ethical hacking skills and uncover potential security weaknesses before they can be exploited by malicious actors.
Key Features:
Rapid Password Cracking: Hydra can quickly test a large number of username and password combinations, making it an effective tool for identifying weak or compromised credentials.
Versatile Access Attempts: The tool can be used to target various services and protocols, including FTP, SSH, HTTP, and more, expanding its utility for ethical hacking.
Responsible Usage: When used responsibly by ethical hackers, Hydra can be an invaluable tool for identifying and addressing security vulnerabilities.
Termux Compatibility: The Termux version of Hydra allows you to run the password-cracking tool conveniently on your Android device, providing mobile penetration testing capabilities.
Fsociety Toolkit Integration: Hydra is seamlessly integrated into the Fsociety Hacking Toolkit, making it easily accessible and part of a comprehensive suite of ethical hacking tools.
How to install Hydra in Termux:
pkg update && pkg upgrade -ypkg install hydraThat's it you have installed Hydra in the Termux. To see the usage of Hydra, type the following command:
hydra -hThe above command will guide you on how to use Hydra in Termux.
Once setup, you can launch dictionary attacks to evaluate authentication mechanisms across apps, systems and networks.
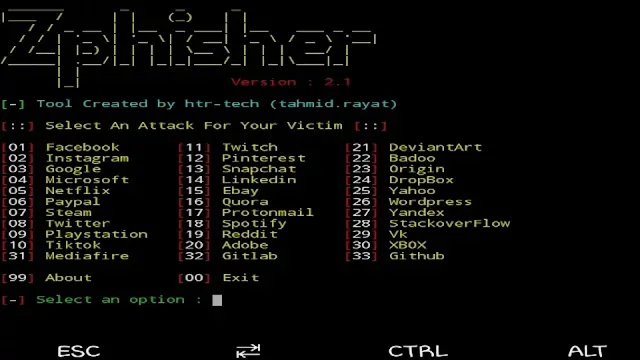
10. Zphisher
Zphisher is a tool that can create fake login pages mimicking popular websites like Facebook and Gmail.
While this may sound concerning, Zphisher is designed for ethical hacking and security testing purposes only, with the goal of raising awareness about phishing tactics.
By using Zphisher responsibly on your Android device, you can gain valuable insights into the world of phishing attacks and take proactive steps to protect yourself and others from falling victim to such malicious tactics.
Key Features:
Realistic Phishing Pages: Zphisher can generate highly convincing fake login pages that closely resemble the real thing, demonstrating how phishing attacks can appear legitimate.
Consent-Based Usage: Zphisher is meant to be used only with the consent of the target audience, not for real credential theft or hacking activities.
Experiential Learning: By using Zphisher, you can gain firsthand experience in understanding how phishing attacks work and the importance of verifying the authenticity of login pages.
Awareness Raising: Properly used, Zphisher can be a valuable tool for educating people about the dangers of phishing and the need to be vigilant when providing their login credentials online.
Android Compatibility: You can access and use Zphisher on your Android device, making it a convenient tool for security awareness and testing purposes.
How to install Zphisher in Termux:
pkg update && pkg upgrade -yapt install git curl php openssh -ygit clone git://github.com/htr-tech/zphisher.gitcd zphisherAccess the utility by typing:
bash zphisher.shRelated Article - How To Install ZPhisher on Termux
11. IPTracer
IPTracer is a remarkable tool that can geolocate the physical, real-world location of an IP address or website domain by cross-referencing IP geolocation databases.
This powerful capability can be a valuable asset for anyone interested in understanding the limitations of online anonymity.
By using IPTracer on your Android device, you can gain a deeper understanding of the limitations of online anonymity and the importance of considering the broader implications of digital footprints.
This knowledge can be invaluable for those interested in cybersecurity, privacy, or simply exploring the intricacies of the digital world.
Key Features:
Pinpoint Physical Locations: When provided an IP address or URL, IPTracer can display the mapped street address location for that online connection or web server.
Demonstrate Anonymity Challenges: The tool highlights how difficult it can be to maintain complete anonymity online based solely on an IP address or website.
Comprehensive Geolocation Data: IPTracer leverages various IP geolocation databases to provide detailed location information, including latitude, longitude, and even the specific street address.
User-Friendly Interface: The tool offers a straightforward and intuitive interface, making it easy for users of all skill levels to explore the capabilities of IP geolocation.
Android Accessibility: With IPTracer available on your Android device, you can conveniently uncover the physical location of online entities wherever you go.
How to install IPTracer in Termux:
apt updateapt install git -ygit clone https://github.com/rajkumardusad/IP-Tracer.gitcd IP-Tracerchmod +x installsh install or
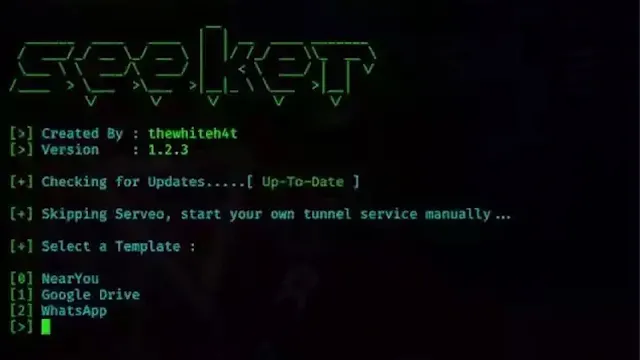
./install12. Seeker
Seeker is an impressive tool that can retrieve precise GPS coordinates by identifying the MAC addresses of devices.
Instead of providing vague location data, it offers exact details like longitude, latitude, city, and even street numbers, allowing you to pinpoint the exact location of your own devices with just a few clicks.
By leveraging Seeker on your Android device, you can gain unprecedented insights into the precise locations of your own devices, as well as explore the potential uses and implications of such advanced GPS tracking tools.
This knowledge can be invaluable for anyone interested in security, privacy, or the evolving landscape of digital technology.
Key Features:
Precise Location Tracking: Seeker can retrieve highly accurate GPS coordinates, giving you the exact longitude, latitude, city, and street number of the tracked device.
Proximity Range Estimation: The tool can also estimate the proximity range of the device you're tracking, providing even more valuable location details.
Useful for Security Research: When used responsibly and ethically, Seeker can be an incredibly valuable tool for security research and understanding the implications of device tracking.
Intuitive Interface: The tool offers a straightforward and user-friendly interface, making it accessible for users of all skill levels.
Android Compatibility: You can access and utilize Seeker on your Android device, allowing you to explore its capabilities on-the-go.
How to install Seeker in Termux:
sudo apt-get updatesudo apt-get install python3 python3-pip php ssh gitpip3 install requestsgit clone https://github.com/thewhiteh4t/seekercd seekerpython3 ./seeker.py -hWrapping Up
These tools can help you learn about computer security in a responsible way. You'll use them to find and fix weaknesses in computer systems. This way, you can make things safer for everyone.
Remember, these tools are only for learning and testing things you're allowed to test. You should never use them to cause harm or break the law.
If you discover any other awesome tools that could teach us more about keeping computers secure, let me know!
And the best part is, you don't need to root your Android device to use these tools. You can use all the ethical hacking tools mentioned here for Termux without needing to root your phone.
By using these tools, you can gain valuable knowledge and skills in cybersecurity, all while making a positive impact. Keep learning, keep exploring, and stay safe!
Related Article - How to install Wireshark in Termux Android: Without root





Post a Comment